Unicorn team are information security researchers who often also dabble with wireless security research. Recently they have been promoting their upcoming text book titled "Inside Radio: An Attack and Defense Guide".
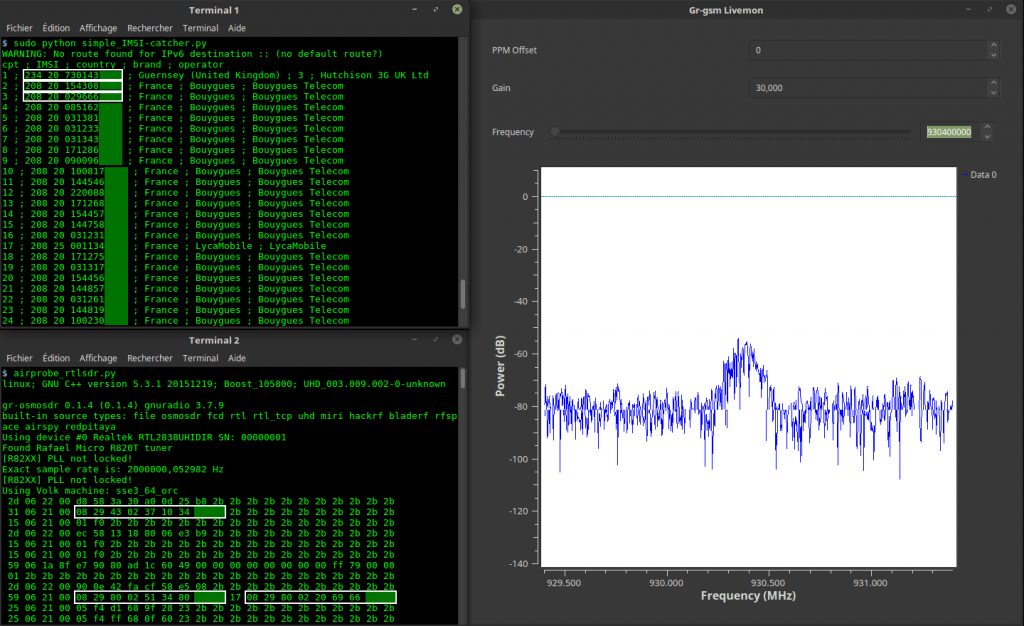
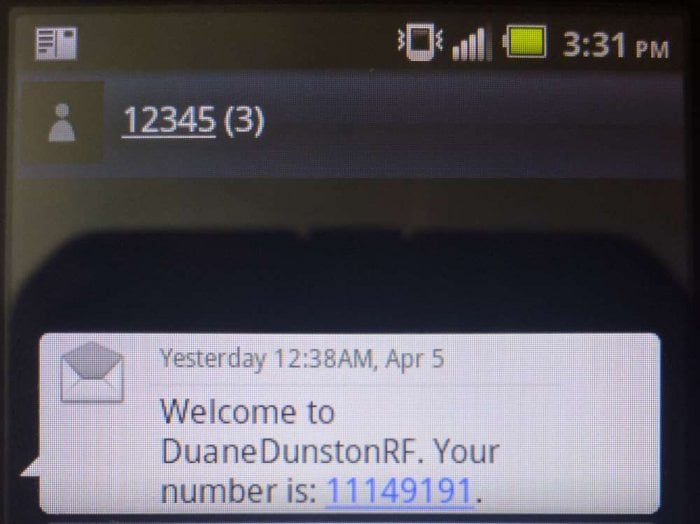
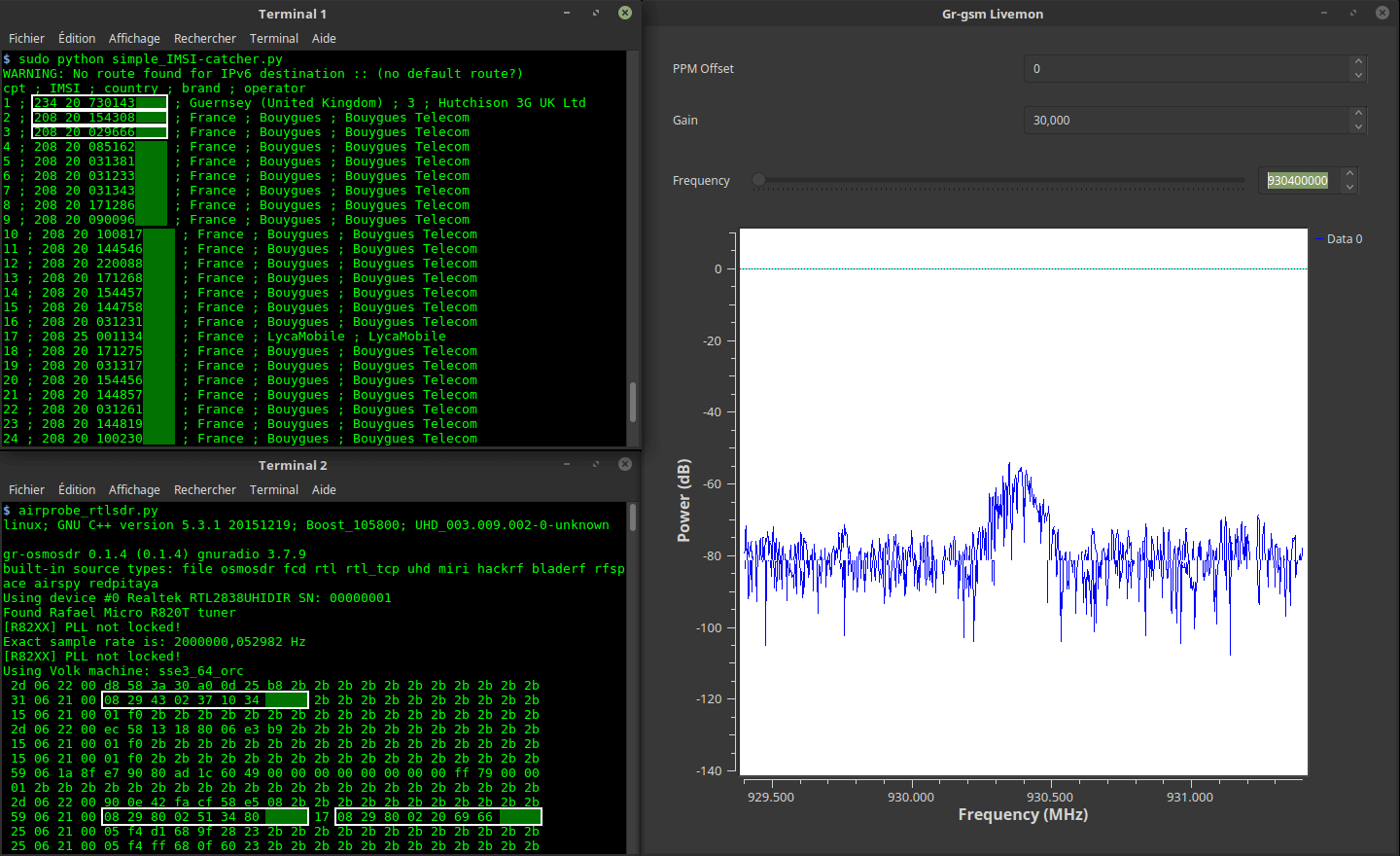
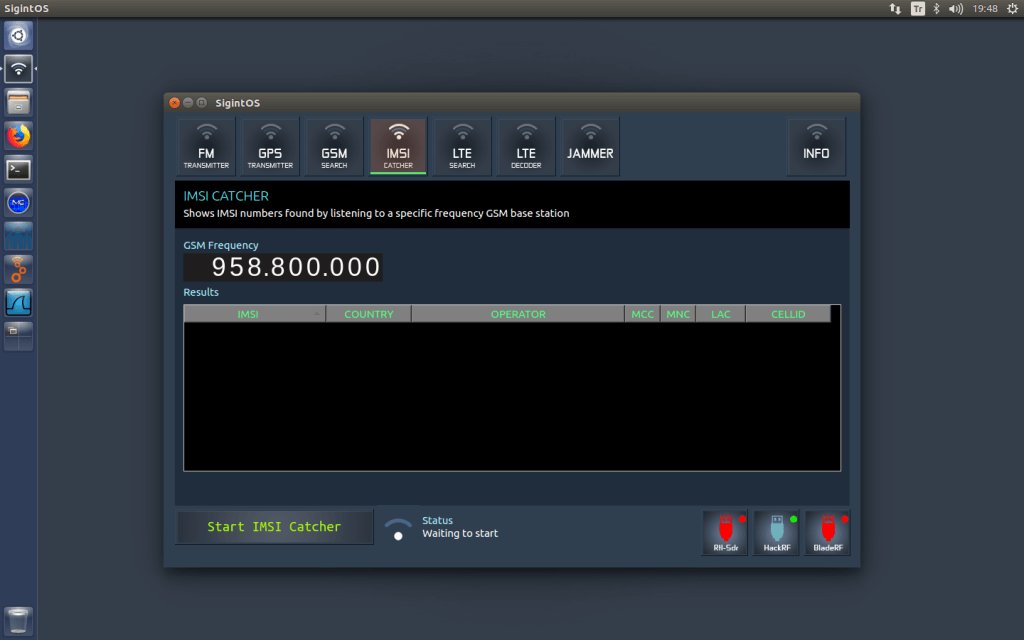
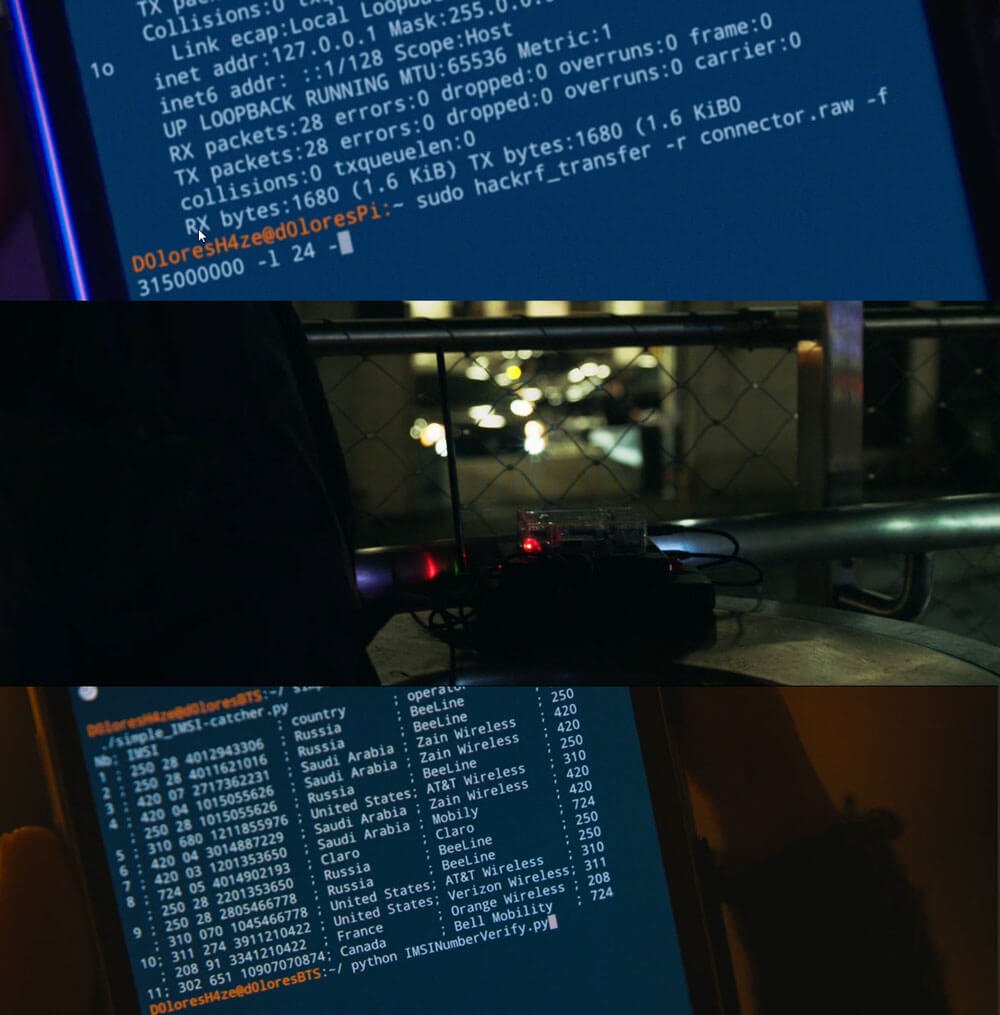
Judging from the blurb and released contents the book will be an excellent introduction to anyone interested in today's wireless security issues. They cover topics such as RFID, Bluetooh, ZigBee, GSM, LTE and GPS. In regards to SDRs, the book specifically covers SDRs like the RTL-SDR, HackRF, bladeRF and LimeSDR and their role in wireless security research. They also probably reference and show how to use those SDRs in the chapters about replay attacks, ADS-B security risks, and GSM security.
The book is yet to be released and is currently available for pre-order on Amazon or Springer for US$59.99. The expected release date is May 9, 2018, and copies will also be for sale at the HITB SECCONF 2018 conference during 9 - 13 April in Amsterdam.
The blurb and released contents are pasted below. See their promo page for the full contents list:
This book discusses the security issues in a wide range of wireless devices and systems, such as RFID, Bluetooth, ZigBee, GSM, LTE, and GPS. It collects the findings of recent research by the UnicornTeam at 360 Technology, and reviews the state-of-the-art literature on wireless security. The book also offers detailed case studies and theoretical treatments – specifically it lists numerous laboratory procedures, results, plots, commands and screenshots from real-world experiments. It is a valuable reference guide for practitioners and researchers who want to learn more about the advanced research findings and use the off-the-shelf tools to explore the wireless world.
Authors:
Qing YANG is the founder of UnicornTeam & the head of the Radio Security Research Department at 360 Technology. He has vast experience in information security area. He has presented at Black Hat, DEFCON, CanSecWest, HITB, Ruxcon, POC, XCon, China ISC etc.
Lin HUANG is a senior wireless security researcher and SDR technology expert at 360 Technology. Her interests include security issues in wireless communication, especially cellular network security. She was a speaker at Black Hat, DEFCON, and HITB security conferences. She is 360 Technology’s 3GPP SA3 delegate.
This book is a joint effort by the entire UnicornTeam, including Qiren GU, Jun LI, Haoqi SHAN, Yingtao ZENG, and Wanqiao ZHANG etc.
![]()
The post Upcoming Book “Inside Radio: An Attack and Defense Guide” appeared first on rtl-sdr.com.